- Winner Digital Transformation Solutions
- Recognized Leader in Cyber Security
- Best Value for Tech Deployment & Project Management


Features
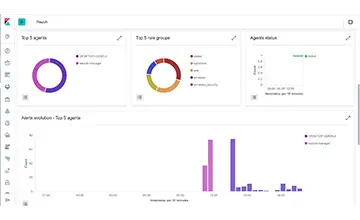
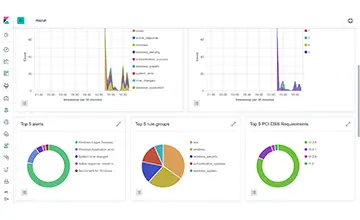

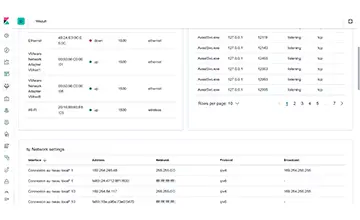

Services
Our engineers provide quick answers to your solution-related questions and issues.
* A dedicated team of engineers
* Periodic health checks and upgrades to the latest version
* Customer satisfaction guaranteed
* Automation of deployment
* Solution configuration, bug fixes and upgrades
* 24/7 support (premium)
*Faster response times (premium)
* More health checks per year (premium)
We carefully analyze your designed environment and create successful architecture, configuration, and integrations with third-party tools.
* Technical assistance
* Troubleshooting
* Support for J-SEP
Our hands-on course covers J-SEP architecture, integrations with Elastic Stack and Splunk, file integrity monitoring, log collection and analysis, vulnerability detection, compliance and policy enforcement
* Three day course
* Course material
* Discover good practices
How can we help you ?
Contacts